Botnet behaviour analysis: How would a data analytics-based system with minimum a priori information perform?
Abstract
Botnets, as one of the most aggressive threats, has used different techniques, topologies, and communication protocols in different stages of their lifecycle since 2003. Hence, identifying botnets has become very challenging specifically given that they can upgrade their methodology at any time. Various detection approaches have been proposed by the cyber-security researchers, focusing on different aspects of these threats. In this work, 5 different botnet detection approaches are investigated. These systems are selected based on the technique used and type of data used where 2 are public rule–based systems (BotHunter and Snort) and the other 3 use machine learning algorithm with different feature extraction methods (packet payload based and traffic flow based). On the other hand, 4 of these systems are based on a priori knowledge while one is using minimum a priori information. The objective here is to evaluate the effectiveness of these approaches under different scenarios (eg, multi-botnet and single-botnet classifications) as well as exploring how a system with minimum a priori information would perform. The goal is to investigate if a system with minimum a priori information could result in a competitive performance compared to systems using a priori knowledge. The evaluation is shown on 24 publiclymore »
- Authors:
-
- Dalhousie Univ., Halifax, NS (Canada). Faculty of Computer Science
- Publication Date:
- Research Org.:
- Lawrence Berkeley National Laboratory (LBNL), Berkeley, CA (United States). National Energy Research Scientific Computing Center (NERSC)
- Sponsoring Org.:
- USDOE
- OSTI Identifier:
- 1543482
- Resource Type:
- Accepted Manuscript
- Journal Name:
- International Journal of Network Management
- Additional Journal Information:
- Journal Volume: 27; Journal Issue: 4; Journal ID: ISSN 1055-7148
- Country of Publication:
- United States
- Language:
- English
- Subject:
- 97 MATHEMATICS AND COMPUTING; computer science; telecommunications; botnet behavior; data analytics; machine learning; network flow analysis
Citation Formats
Haddadi, Fariba, and Zincir-Heywood, A. Nur. Botnet behaviour analysis: How would a data analytics-based system with minimum a priori information perform?. United States: N. p., 2017.
Web. doi:10.1002/nem.1977.
Haddadi, Fariba, & Zincir-Heywood, A. Nur. Botnet behaviour analysis: How would a data analytics-based system with minimum a priori information perform?. United States. https://doi.org/10.1002/nem.1977
Haddadi, Fariba, and Zincir-Heywood, A. Nur. Tue .
"Botnet behaviour analysis: How would a data analytics-based system with minimum a priori information perform?". United States. https://doi.org/10.1002/nem.1977. https://www.osti.gov/servlets/purl/1543482.
@article{osti_1543482,
title = {Botnet behaviour analysis: How would a data analytics-based system with minimum a priori information perform?},
author = {Haddadi, Fariba and Zincir-Heywood, A. Nur},
abstractNote = {Botnets, as one of the most aggressive threats, has used different techniques, topologies, and communication protocols in different stages of their lifecycle since 2003. Hence, identifying botnets has become very challenging specifically given that they can upgrade their methodology at any time. Various detection approaches have been proposed by the cyber-security researchers, focusing on different aspects of these threats. In this work, 5 different botnet detection approaches are investigated. These systems are selected based on the technique used and type of data used where 2 are public rule–based systems (BotHunter and Snort) and the other 3 use machine learning algorithm with different feature extraction methods (packet payload based and traffic flow based). On the other hand, 4 of these systems are based on a priori knowledge while one is using minimum a priori information. The objective here is to evaluate the effectiveness of these approaches under different scenarios (eg, multi-botnet and single-botnet classifications) as well as exploring how a system with minimum a priori information would perform. The goal is to investigate if a system with minimum a priori information could result in a competitive performance compared to systems using a priori knowledge. The evaluation is shown on 24 publicly available botnet data sets. Results indicate that a machine learning–based system with minimum a priori information not only achieves a very high performance but also generalizes much better than the other systems evaluated on a wide range of botnet structures (from centralized to decentralized botnets).},
doi = {10.1002/nem.1977},
journal = {International Journal of Network Management},
number = 4,
volume = 27,
place = {United States},
year = {Tue May 09 00:00:00 EDT 2017},
month = {Tue May 09 00:00:00 EDT 2017}
}
Web of Science
Figures / Tables:
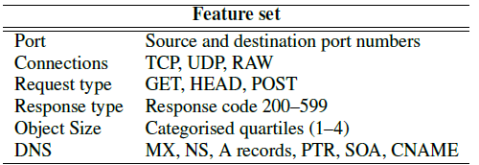 Table I: Packet-based approach– network features.
Table I: Packet-based approach– network features.
Works referenced in this record:
A fuzzy pattern-based filtering algorithm for botnet detection
journal, October 2011
- Wang, Kuochen; Huang, Chun-Ying; Lin, Shang-Jyh
- Computer Networks, Vol. 55, Issue 15
An empirical comparison of botnet detection methods
journal, September 2014
- García, S.; Grill, M.; Stiborek, J.
- Computers & Security, Vol. 45
Botnet Detection Based on Network Behavior
book, January 2008
- Strayer, W. Timothy; Lapsely, David; Walsh, Robert
- Botnet Detection
Machine learning algorithms for accurate flow-based network traffic classification: Evaluation and comparison
journal, June 2010
- Soysal, Murat; Schmidt, Ece Guran
- Performance Evaluation, Vol. 67, Issue 6
Benchmarking the Effect of Flow Exporters and Protocol Filters on Botnet Traffic Classification
journal, December 2016
- Haddadi, Fariba; Zincir-Heywood, A. Nur
- IEEE Systems Journal, Vol. 10, Issue 4
An Overview of IP Flow-Based Intrusion Detection
journal, January 2010
- Sperotto, A.; Schaffrath, G.; Sadre, R.
- IEEE Communications Surveys & Tutorials, Vol. 12, Issue 3
CoCoSpot: Clustering and recognizing botnet command and control channels using traffic analysis
journal, February 2013
- Dietrich, Christian J.; Rossow, Christian; Pohlmann, Norbert
- Computer Networks, Vol. 57, Issue 2
On the Effectiveness of Different Botnet Detection Approaches
book, January 2015
- Haddadi, Fariba; Le Cong, Duc; Porter, Laura
- Information Security Practice and Experience
Clustering botnet communication traffic based on n-gram feature selection
journal, March 2011
- Lu, Wei; Rammidi, Goaletsa; Ghorbani, Ali A.
- Computer Communications, Vol. 34, Issue 3
Botnet detection based on traffic behavior analysis and flow intervals
journal, November 2013
- Zhao, David; Traore, Issa; Sayed, Bassam
- Computers & Security, Vol. 39
An Effective Network Traffic Classification Method with Unknown Flow Detection
journal, June 2013
- Jun Zhang,
- IEEE Transactions on Network and Service Management, Vol. 10, Issue 2
Coevolutionary bid-based genetic programming for problem decomposition in classification
journal, July 2008
- Lichodzijewski, Peter; Heywood, Malcolm I.
- Genetic Programming and Evolvable Machines, Vol. 9, Issue 4
Works referencing / citing this record:
Botnet detection based on network flow summary and deep learning
journal, July 2018
- Pektaş, Abdurrahman; Acarman, Tankut
- International Journal of Network Management, Vol. 28, Issue 6
Deep learning to detect botnet via network flow summaries
journal, July 2018
- Pektaş, Abdurrahman; Acarman, Tankut
- Neural Computing and Applications, Vol. 31, Issue 11
A novel network virtualization based on data analytics in connected environment
journal, October 2018
- Bui, Khac-Hoai Nam; Cho, Sungrae; Jung, Jason J.
- Journal of Ambient Intelligence and Humanized Computing, Vol. 11, Issue 1
An Adaptive Multi-Layer Botnet Detection Technique Using Machine Learning Classifiers
journal, June 2019
- Khan, Riaz Ullah; Zhang, Xiaosong; Kumar, Rajesh
- Applied Sciences, Vol. 9, Issue 11
Figures / Tables found in this record:

 Search WorldCat to find libraries that may hold this journal
Search WorldCat to find libraries that may hold this journal